
WhireShark is a tool for network analysis. It register all packets pass into a selected network interface (including wireless LAN). It also can be useful combined with arp poisoning attack using arpspoofing technique. It should be used by everyone network manager because it captures packets and lets you examine their contents. It is an open source software released under GNU General Public License (GPL) and you can use it on any number of computers you like. This allow people to add new plugins to WhireShark.
Unlike Burp Suite, WhireShark can’t manipulate things on the network and can’t send packets, it only register things from the network.
Wireshark also can open packets captured from others capture programs and it can save packets captured in a large number of formats of other capture programs.

This is the entry screen, in which you can see all available network connections on your current device and that permit you to select the network of which you are interested in capturing packages. After selecting it and after starting to capture the packages, the screen will be as follows:

This is the main windows and it is divided in 3 sections:
1. The “Packet List” section:

This panel shows all packets captured, one per line. You can select a package for see it in the section below. It’s possible to filter packages by choice using a “filter bar” (see “WireShark Filter”).
2. The “Packet Details” section:
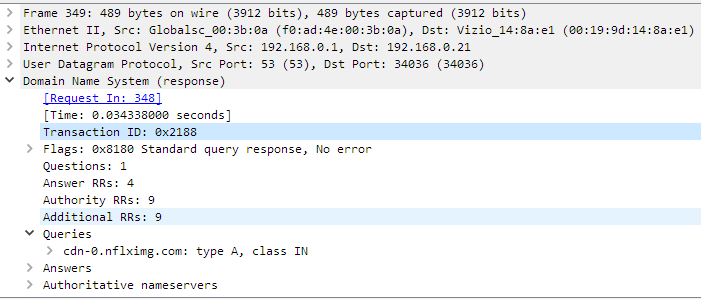
It shows the fields of selected packet, in a collapsible format.
3. The “Packet Bytes” section:
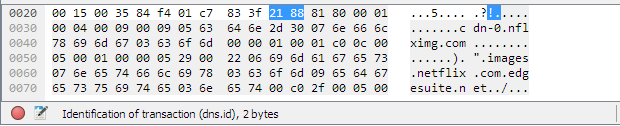
It displays the raw data of the selected packet in a hexadecimal view. This hex dump contains 16 hexadecimal bytes and 16 ASCII bytes alongside the data offset. You can choose to show this data in bit format by right-clicking anywhere within the panel and selecting the appropriate option from the context menu.
WireShark Filter
When, in a packets capture, you are interested in only some types of packets, you can apply WireShark filter, especially when you’re dealing with many packets and with files that are significant in size. There are a large number of predefined filters and you can select one of these writing it in the “Apply a display filter” bar immediately above “Packet List” section. This will permit you to see only filtered packets. Some examples of simple filtering:
host 192.168.1.74
it filters only traffic to or from one specific device;
net 192.168.1.0/24
it filter entire net traffic;
port 53
only port 53 traffic;
tcp
only tcp traffic;
udp
only udp traffic;
http||arp
http and arp traffic;
ip.src == 192.168.1.1
only packets that have source IP 192.168.1.1.
Some other examples of more complex filtering:
tcp.port==23 and host==192.168.1.24
only telnet traffic for only one specific host;
tcp.port==23 and not host==192.168.1.24
only telnet traffic for all host except selected one;
http.user_agent contains Firefox
it filters user agent;
!http.user_agent contains Firefox || !http.user_agent contains Chrome
this filters out all user agents that contain Firefox or Chrome;
tcp.port 80 && ip.addr == 192.168.1.55
this shows only port 80 that has IP 192.168.1.55 in the source or destination;
http.host matches "test\.(org|com|net)"
it matchs HTTP packets where the HOST header contains test.org or test.com or test.net.
WhireShark Filters Operators examples:
and, &&
logical AND
or, ||
logical OR
not, !
logical NOT
eq, ==
equal
ne, !=
not equal
gt, >
greater
lt, <
lower
ge, >=
greater or equal
le, <=
lower or equal
That said, you can imagine the importance and usefulness of this tool in the pentest job.